Revolutionizing Connectivity: The Transformative Role of AI in Global Telecommunications
Artificial Intelligence is changing the way telecommunications companies do business.

Telecommunications systems have become the lifeblood of global commerce and civilization. Reliable, efficient connectivity has never been more crucial. The demand for reliable telecommunications services continues to soar, and as this demand intensifies, so does the pressure on telecom companies to keep pace with a host of ever-evolving technologies.
One suddenly ubiquitous technological disruptor that’s dramatically reshaping the telecom landscape is artificial intelligence (AI). AI’s abilities to automate processes; analyze vast amounts of data; work endlessly without need of food, sleep, or wages; and optimize network performance are revolutionizing the telecommunications industry, often in ways no one could have envisioned.
AI has proven to be beyond disruptive as it impacts cultures, transforms industries, and creates new challenges and opportunities. Almost daily, we witness new evidence of its evolution: creating astonishing artwork and poetry, engaging in (usually) polite and intelligent conversation, even operating vehicles on the highway while only killing a few human beings in the process. Love it or hate it, AI has arrived and is here to stay.
So, what does this mean for the telecommunications industry?
It means artificial intelligence is already a big part of our work lives, used for such purposes as failure detection, network and traffic-demand prediction, network architecture design, and network rollouts.
Currently, some of the most highly visible applications of AI in telecommunications are:
- Modeling predictive maintenance,
- Optimizing network traffic to prevent congestion,
- Personalizing automated customer-service interactions,
- Tailoring service offerings to individual customers, and
- Improving the efficiency of emergency-response services.
Wait another ten minutes, though, and the list will no doubt double or triple.

Predictive Maintenance
AI is having a substantial impact on the cost efficiency of telecommunications operations through the process of predictive maintenance. Telecommunication networks consist of thousands of components, from antennas to routers, which require regular maintenance to ensure optimal performance. Scheduling maintenance based on fixed intervals can be inefficient and costly; AI-driven predictive maintenance determines the condition of network components to calculate when maintenance should be performed. Through continuous data analysis from sensors installed and embedded across a network, predictive AI algorithms can detect early indications of equipment degradation having the potential to create a system-impacting failure. If a system sensor detects an anomaly, the AI can issue an alert so that technicians can address the issue before it escalates—potentially averting a network outage that might have disrupted communication services for millions of users.
AT&T, a global leader in telecommunications, is among the industry’s major players to have implemented AI-driven predictive maintenance solutions. By analyzing data from sensors installed across its network infrastructure, AT&T can predict equipment failures before they occur. This proactive approach to maintenance has resulted in lower maintenance costs and increased network uptime, leading to increased customer satisfaction and loyalty.
According to John Smith, AT&T’s Chief Operating Officer, “AI has transformed our maintenance operations, allowing us to move from reactive to proactive maintenance. By identifying potential issues in advance, we can schedule repairs more efficiently and minimize downtime for our customers.”
AI-Driven Network Optimization
Another AI-driven function massively impacting the telecommunications space is network optimization. Traditional networks often struggle to handle sudden, massive influxes of data traffic, leading to congestion and service disruptions, but AI-driven network-optimization solutions are changing the game.
British Telecom (BT), a global leader among telecommunications providers, has been using advanced machine-learning algorithms to predict network failures before they occur. These algorithms, part of BT’s AI-powered network-optimization system, enable the AI to analyze historical data to identify patterns and anomalies, allowing BT to address potential network traffic issues proactively and ensure uninterrupted service for its customers.
“AI has been instrumental in enhancing the reliability and performance of our network infrastructure,” said Dr. Sarah Jones, CTO at British Telecom. “By predicting and preventing network failures, we can minimize downtime and deliver a better customer experience.”
Acme Telecom, a medium-sized Indian telecommunications company, also faced challenges in managing its infrastructure. The Acme network was becoming increasingly congested, leading to frequent service disruptions and frustrated customers. In response, Acme implemented an AI-driven network-optimization solution that analyzes vast amounts of data in real time, identifying bottlenecks and optimizing routing to ensure smooth traffic flow.
The results were immediate and significant. During a recent major sporting event that Acme’s network had often struggled to handle in previous years, the AI-optimization system managed the surge in data traffic and kept the network stable, maintaining uninterrupted service for thousands of customers. Since implementing the AI solution, Acme has reported significantly decreased network congestion and increased customer satisfaction scores.

Large telecommunications businesses have never been lauded for their outstanding customer service; that’s because they’ve never had any. Thankfully, customer service is yet another area of telecom that AI is rapidly transforming. The frustrating old days of interminable waiting on hold to speak to a surly, overwhelmed, or incomprehensible human “customer service” agent are almost over. AI-powered chatbots now handle a significant portion of customer inquiries, and they’re doing so quickly and efficiently.
Verizon, one of the world’s largest telecommunications operations, is employing AI chatbots to handle routine customer queries. These chatbots use natural-language processing (NLP) to comprehend customer requests and provide relevant, real-time responses. As a result, Verizon has seen a significant reduction in hold times and a corresponding increase in customer satisfaction.
“AI chatbots have revolutionized our customer-service operations,” says Maria Rodriguez, Vice President of Customer Experience at Verizon. “They allow us to provide 24/7 support, resolving issues quickly and efficiently. The result has been higher customer-satisfaction scores and reduced operating costs for the company.”
Targeting Service Offerings More Effectively
Telecom firms are also using AI to tailor and personalize the services they offer to their customers. AI algorithms can analyze customer data to identify preferences and behavior patterns, enabling providers to target their promotions and offerings.
Vodafone, a leading British multinational telecommunications company, has implemented AI-powered “recommendation engines” to personalize its offerings. These engines analyze customer usage data to recommend the most suitable plans and services to each customer. As a result, Vodafone has seen an increase in customer loyalty and satisfaction.
“AI has allowed us to offer personalized services that resonate with our customers,” said Emily Johnson, Vodafone’s Chief Marketing Officer. “Since we understand their preferences and behavior, we can tailor our offerings to meet their needs.”
Improving Emergency Services
When you dial 9-1-1, your call is routed to a Public Safety Answering Point (PSAP), usually operated by a state or local government. Today, many of these PSAP centers are struggling to fill open positions, impacting their ability to respond to 9-1-1 calls in a time frame that their communities expect. PSAPS are increasingly turning to artificial intelligence (AI) to tackle these staffing shortages and enhance emergency-response efficiency. AI technologies can streamline call routing, prioritize emergency calls, and even provide initial assessments of situations, thus reducing the workload on human operators. AI systems can analyze incoming calls, extracting crucial information like the location and nature of the emergency, as well as suggest appropriate responses. This expedites the dispatch process and enables human operators to focus on more complex situations.
Artificial Intelligence is profoundly transforming the telecommunications industry, from network optimization to customer service and way, way beyond. By harnessing the power of AI, telecommunications firms can improve efficiency, enhance customer experience, and stay ahead of the competition.

The 988 system can provide our military service members with the resources to prevent a crisis from becoming a tragedy.
Sergeant John H. understood fighting—the dangers, the enemy, the adrenaline rush, the brotherhood. A combat veteran on this third overseas tour, he was ready to face whatever came at him head-on.
Or so he thought.
On his return home, John realized he was struggling with a host of unseen internal adversaries: PTSD, feelings of isolation, and a general alienation from civilian life. His attempts to resolve these issues through self-medication, withdrawal, and reckless impulsivity probably sound disturbingly familiar to many veterans and their loved ones; things quickly went from bad to unsustainable.
After months of suffering in silence and explosive frustration, John finally mustered the courage to seek help. He picked up his cellphone and dialed “988,” then pressed “1.”
Over the following year, through compassionate listening and supportive, expert guidance, he found the path he desperately needed to begin his long journey toward healing.
In the ongoing struggle against the devastating epidemic of military suicides, a powerful new tool has arisen: the Veterans/Military Crisis Line system. As a crucial lifeline for active-duty personnel and veterans alike, this system can serve as a beacon of hope, offering immediate support and intervention to those in crisis. The Veterans/Military Crisis Line system is a game-changer in the fight to heal the souls and save the lives of our most fearless and honorable citizens.
The Foundation: Understanding the 988 System
In July 2020, the Federal Communications Commission (FCC) unanimously voted to establish 988 as the new three-digit number for the National Suicide Prevention Lifeline—this decision aimed at simplifying access to mental health support and reducing the stigma associated with seeking help. Callers are directly connected with mental health professionals trained in suicide prevention and crisis counseling.
The Unique Needs of Military Personnel
While the implementation of 988 was a significant step forward in addressing America’s mental-health crises, it soon became evident that veterans, active-duty military personnel, and their families faced unique challenges—deployments, combat exposure, the transition to and from civilian life—that required mental-health support tailored to their unique experiences. Recognizing this, the Veterans Administration (VA) and the Department of Defense (DoD) began planning on the integration of the “988 + 1” dialing capability within the DoD unclassified telephone network to ensure military members can access the Veterans Crisis Line (VCL) at any time.
Building upon the infrastructure established for the National Suicide Prevention Lifeline (988), the DoD integrated the “988 + 1” capability into existing DoD telephone systems, ensuring seamless coordination between the civilian and military telephone networks. This allowed access to VA mental-health support professionals and enabled service members to access support from any unclassified DoD telephone.
The resulting system is a specialized helpline designed to provide mental-health support and crisis intervention tailored explicitly to military members, veterans, and their families. Service members dialing “988” and pressing “1” are immediately connected to VCL professionals whose training and personal experience qualify them to understand the unique challenges and experiences faced by those who have served in the armed forces. By offering a confidential and judgment-free space to talk about their struggles, the 988 + 1 service can provide service members with the assistance and resources they need to prevent a crisis from becoming a tragedy.
Immediate Availability: Reaching Military Members Anywhere
Early intervention is a critical element in preventing military suicides, and the 988 + 1 system plays a pivotal role in providing immediate support to those in crisis, regardless of their geographical location. Service members can access the counseling and support they need from any DoD telephone switch, however remote, simply by dialing the designated number. This level of accessibility is crucial, as it ensures that no individual is left to struggle alone, even in distant or isolated locations.
The VCL infrastructure was completed in 2022, and the 9-8-8 dialing capability was officially activated on all U.S. military installations in the same year. Ongoing monitoring and evaluation mechanisms were established to assess the hotline’s effectiveness and identify areas for improvement, allowing for continuous refinement of the system to meet the evolving needs of the military community. As of January 2024, the VCL has taken over 7.6 million calls, 360,000 texts, and 910,000 online chats since its establishment.
To ensure that service members knew about the new service and how to use it, the DoD launched training and awareness campaigns at its camps, posts, and bases worldwide. These campaigns included educational materials, briefings, and outreach efforts to promote mental health awareness and encourage help-seeking behaviors among service members.
Chat and SMS Messaging for the Veterans/Military Crisis Line Service
Recognizing the importance of providing multiple options for those seeking assistance and the communications preferences of the DoD’s younger members, the VCL service also includes chat (https://www.veteranscrisisline.net/get-help-now/chat) and SMS (Text 838255) messaging capabilities. These allow service members to access support discreetly and conveniently, especially in environments or operations where making a phone call might not be a realistic option.
The Voice on the other End of the Line
The mental health specialists and counselors who field incoming communications within the 988 + 1 system undergo intense, specialized training and education to enable them to understand and address the unique challenges military personnel face. This training includes cultural sensitivity, understanding the military lifestyle, and familiarity with resources available to service members and their families.
The work of these specialists and counselors can often mean the difference between life and death. Consider the case of Sarah K., a military spouse grappling with the stresses of multiple deployments and the strain they placed on her family. Feeling overwhelmed and alone, Sarah dialed 988 + 1 and was met with immediate empathy and understanding. The counselor on the other end of the line listened to Sarah without judgment, offering support and resources that ultimately guided her forward. Sarah said, “The support I received helped me cope with the challenges I was facing and strengthened my resilience and sense of community.”
John Smith, a 988 + 1 Counselor, notes, “Working with military personnel through 988 + 1 has been incredibly rewarding. We can provide tailored support that acknowledges the unique challenges they face.”
Dr. Sarah Johnson, a Mental Health Specialist, concurs: “The feedback we receive from callers who have used 988 + 1 is overwhelmingly positive. They appreciate the anonymity, understanding, and resources we offer.”
While these testimonials provide subjective insight into the positive impact of 988 + 1, it’s important to continue gathering data and conducting research to assess its effectiveness. As the system continues to evolve and expand, ongoing evaluation will be essential in refining and optimizing its services to serve the mental health needs of military personnel.
As we continue to combat the epidemic of military suicides, the importance of the Veterans/Military Crisis Line system cannot be overstated. It is a testament to our commitment to honoring the sacrifices of those who have served by ensuring they receive the care and support they deserve. As we strive for a future where no service member needs to suffer in silence, the Veterans/Military Crisis Line hotline helps ensure that help is always within reach.


Women’s History Month is the perfect time to spotlight the often-unsung heroines who have shaped our modern telecommunications landscape. As is nearly always the case within rapidly evolving fields, small businesses have emerged as hotbeds of telecom innovation and opportunity, and women have played a crucial role in propelling this extraordinary progress.
Today, we examine the inspiring stories of four female telecommunications professionals at one such company: Netmaker Communications, a small, FCC-registered telephone company in Virginia’s Shenandoah Valley. As they solve customers’ hardware and software problems, configure and administer complex customer networks, and hover as sentinels in the dark world of cybersecurity, these women are central to Netmaker Communications’ growing prominence within the industry.

Ashley Litaker, Systems Administrator/VoIP Engineer
Ashley Litaker plans, designs, configures, and deploys the networked systems that form the basis of Netmaker Communications’ commercial operation. With years of experience in numerous telecommunications technologies, Ashley sits at the nexus between Netmaker Communications’ services and its clients, troubleshooting problems and preparing the launch of new systems. To say that her work hours are long would be an understatement. Ashley is also the mother of four children, two teenagers and two infants—enough to strain the inner resources of anyone. Sleep, needless to say, is a rare luxury for her. Ashley works remotely when possible—a near necessity for someone who essentially lives two full-time lives simultaneously—which can present its own, often hilarious challenges.
“I was showing a demonstration to a potential customer over Teams,” she explains, “And my bird would not stop squawking in the background. So, I turned and yelled at him at the top of my lungs, thinking I had muted my microphone. But no, I had not. After my screaming, the awkward silence from everyone else on the call was deafening.”Ashley faces the hurdles of being a woman in a predominantly male field with an understated, good-natured equanimity: “At first, I didn’t realize the challenges that would come with being a woman in a male-dominated field. On the one hand, you must work harder to prove you can do the work, but on the other hand … #girlpower!”
Ashley also recently earned a bachelor’s degree in information technology, graduating Summa cum laude. “I hope to set an example for my girls that they can do anything. They can be anything.”
Nichole Johnson, Systems Administrator/ Computer Science Engineer
Nichole Johnson has six children, three of them still living at home. She is also Netmaker Communications’ resident computer science engineer, with two decades of experience in topics ranging from network installation to automated software management and end-user support. Nichole works closely with Ashley to configure and prepare the elaborate Voce-over IP (VoIP) systems that constitute the primary elements of many of the services the company provides. She also assists customers in resolving any problems they’re experiencing with their systems.
Beneath Nichole’s quiet demeanor and extraordinary patience lies a keen and capable mind possessing exceptional technical acumen. A self-professed night owl and workaholic, her sleep schedule would be unsustainable for most of us—particularly with three children to care for. Nichole’s primary motivation for entering the male-dominated field of telecommunications was her children, and she’s never regretted taking the leap. “Being a mother of six, I wanted to be able to provide for my children and make sure they had a comfortable life. Getting a job in high technology almost 20 years ago was the best decision I ever made.”
As Nichole reflects on her time at the firm, it’s clear she’s pleased with her decision to come aboard.
“Working at Netmaker Communications has allowed me to keep expanding my knowledge of the constant changes occurring within the Telecom technology infrastructure,” she says. “I love learning new things, and Netmaker Communications offers me constant challenges to develop and expand my familiarity with the technology’s leading edge.”

Nena Dodson, Senior Telecommunications Engineer
Nena Dodson is among Netmaker Communications’ most important engineers, directly involved in creating complex network structures and managing the company’s data within the core infrastructure of the Netmaker Communications network.
Her work is of the highest importance, and the price for complacency or sloppiness could run into the millions of dollars. Nena’s position at Netmaker Communications is based on her 20-year career in the telecommunications field; she is an expert in communications protocols, network and system administration, and other technical subjects too numerous to mention. Her work week often exceeds 60 hours.
When she first entered the telecommunications field, Nena refused to let anything keep her from charging headlong toward her goals. “I always felt that I had to work harder, be faster, be earlier, stay later, and volunteer more than anyone else. I didn’t see gender,” she adds, “I just wanted to be the best engineer in the office. Everyone saw that, which is why I landed the positions I wanted.”

Carmen Thayer, Junior Cybersecurity Analyst
Carmen Thayer is the newest addition to Netmaker Communications’ team of women serving in telecommunications roles. She started as a summer intern in the cybersecurity department, impressing everyone with her work ethic, and ability to quickly master new tasks.
Then, Netmaker Communications’ director of cybersecurity abruptly left the organization, leaving a critical gap in the company’s cybersecurity capabilities.
Anxious to ensure its cybersecurity functions remained operational, Netmaker Communications asked Carmen if she would like to transition from intern to employee. Carmen agreed, becoming a junior cybersecurity analyst and, simultaneously, the highest-ranking cybersecurity specialist in the company.
The sudden change in status came as a shock to Carmen, who had previously worked as an ice cream vendor: “Nerve-wracking. I am very much aware of my limitations, gaps in knowledge, and areas I need to work on. I like to consider that awareness a strength,” she says, “But I wasn’t expecting a trial-by-fire situation, and while I’m still nervous, I’m not going to back down. I’m lucky and excited to be here.”
When asked about the unique challenges women face in the telecommunications field, Carmen offers a fascinating perspective: “While my sex affects other’s perceptions of me, it does not affect how a computer or firewall will react, and those are the things I care about. I had no say in how I was born, but I can work and grow and improve my skills. I’m not an expert yet, but I’m going to put in the work to become one.”
How does she feel about starting her cybersecurity career at Netmaker Communications?
“I’m grateful and excited. I’ll be a great Cybermancer someday.”
Understanding the differences between Wi-Fi standards can help you make the right decision.
–Lee Curling
Get ready for the incoming wave of Wi-Fi 7 (802.11be) marketing. The messages will be loud and prominent, and they’ll insist that you need to upgrade NOW!
“Marketing through FUD” (Fear, Uncertainty, and Doubt) will be the order of the day.
Of course, there’s a BIG element of truth behind the looming wave; the ever-evolving wireless networking standards play a crucial role in determining the quality of our internet experience. Wi-Fi 6E (802.1X), the current standard, allowed for much faster and more efficient connections. With the official release of Wi-Fi 7 on January 8, 2024, many are eager to explore its advantages over the previous standard, with vendors busily promoting new Wi-Fi 7-compliant products. But before committing to upgrade to the latest and greatest, organizations should understand the current wireless-network landscape and the differences between Wi-Fi 6E and Wi-Fi 7.
The Evolution from Wi-Fi 5 to Wi-Fi 7
The advent of Wi-Fi 6 brought significant speed improvements over its 801.11AC “Wi-Fi 5” predecessor, with features like Orthogonal Frequency Division Multiple Access (OFDMA) and Basic Service Set (BSS) Coloring.
The current Wi-Fi 6E standard added support for the 6 GHz radio band, which opened up new channels to avoid congestion and increase performance while providing a maximum transfer speed of around 9 Gbps.
Wi-Fi 7, on the other hand, can reach speeds of up to 46 Gbps—five times the rate of Wi-Fi 6E. It also introduces techniques such as Multi-User Multiple Input Multiple Output (MU-MIMO) enhancements and makes more robust use of frequency bands.
Wi-Fi 7 increases the number of spatial streams from 8 to 16, doubling the theoretical physical transmission rate. It also introduces a more flexible resource unit (RU) allocation method that provides more efficient channel utilization, making it even more valuable in scenarios where multiple devices are competing for bandwidth.
Certifications and the Device Landscape
While the Wi-Fi 7 specification has been officially released, few devices have undergone the Wi-Fi 7 CERTIFIED program as of this writing. This scarcity of certified devices means that users are unlikely to experience the full spectrum of Wi-Fi 7’s capabilities, as prerelease vendors may only have implemented a subset of the specification’s features. Beware of vendors selling pre-standard devices; if these devices are not fully standards-compliant, you could face compatibility issues and suboptimal performance.
On the mobile client front, The iPhone 15 Pro supports Wi-Fi 6E, while the remainder of the Apple phone lineup supports Wi-Fi 6. There is speculation that the iPhone 16 Pro will support Wi-Fi 7, but it is still just speculation, and it’s a year away(1). Some Android devices are shipping with Wi-Fi 7-capable hardware, but that doesn’t mean they fully support Wi-Fi 7 just yet.
Let’s address the reality behind all these numbers.
Upgrading: Is It Necessary?
1. Everyday Usage:
For typical home and office users engaged in web browsing, video streaming, and regular online activities, Wi-Fi 6 already provides a sufficiently robust and speedy connection. For those users, the perceived improvement in day-to-day performance might not be significant enough to justify an upgrade to Wi-Fi 7.
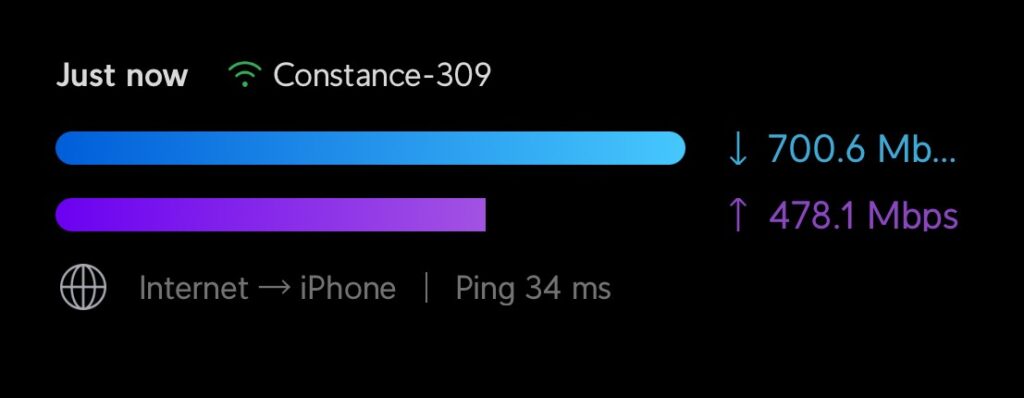
When doing a speed test to the internet, I routinely get download speeds of about 700Mbs with a Wi-Fi 6 client and my Wi-Fi 6 APs; however, I rarely get that speed when actually using the internet due to a number of external factors such as website or download-bandwidth limits, route congestion, and general internet performance.
2. Specific Use Cases:
Wi-Fi 7’s advanced features are best suited to such uses as ultra-high-definition video streaming, augmented reality (AR), virtual reality (VR), and Mixed Reality (MR)(2). If these are not integral to your requirements, the benefits will not justify the upgrade. For example, Wi-Fi 6 handles the current generation of consumer VR systems without issue. Now, if you wanted to have a VR “LAN Party” at your house, that could certainly justify the adoption of Wi-Fi 7. Even the next-generation televisions with 8K resolution will require less than 200Mbs from streaming services, which is well within the Wi-Fi 6 performance curve.
If you are responsible for a high-density wireless location—such as an arena setting that supports concerts or sporting events—then Wi-Fi 7 would be a great choice. In the short term, however, your customers’ devices will still be unable to access the optimizations built into Wi-Fi 7.
3. Device Compatibility:
Consider the devices you currently own. Few devices are Wi-Fi 7 certified at the moment, and the market is flooded with pre-standard devices. As the standard becomes more widely adopted, device compatibility will increase, making the upgrade more significant.
4. Cost Consideration:
Upgrading networking hardware to accommodate Wi-Fi 7 may come with a hefty price tag. Remember that the upgrade needs to be on both the access point and the client side. Given the current device landscape and the improvements that Wi-Fi 7 offers, you’ll have to decide when the investment becomes justifiable.
The Wrap-Up
The release of Wi-Fi 7 adds a new dimension to wireless connectivity with valuable, long-term promise. However, with the limited availability of certified devices and the presence of pre-standard offerings in the market, caution is advised. Assess whether the specific features of Wi-Fi 7 align with your requirements and whether the current device landscape supports a seamless transition. As technology evolves, so will the necessity for upgrades, but for now, it’s essential to make informed choices based on the existing realities of the Wi-Fi 7 ecosystem.
| Wi-Fi 6 vs Wi-Fi 6E vs Wi-Fi 7 | |||
| Wi-Fi-6 | Wi-Fi 6E | Wi-Fi 7 | |
| IEEE Standard | 802.11ax | 802.11ax | 802.11be |
| Wireless Bands | 2.4GHz, 5GHz | 2.4GHz, 5GHz, 6GHz | 2.4GHz, 5GHz, 6GHz |
| Maximum Spatial Streams | 8 | 8 | 16 |
| Maximum Bandwidth per Stream | 1.2 Gbps | 1.2 Gbps | 2.4 Gbps |
| Theoretical Maximum Data Rate | 9.6 Gbps | 9.6 Gbps | 46 Gbps |
Resources:
- iPhone 16 Pro rumors: faster 5G modem, Wi-Fi 7, better ultra-wide (9to5mac.com)
- https://www.rcrwireless.com/20231207/fundamentals/is-there-a-killer-use-case-for-wi-fi-7
NG9-1-1 represents a revolution in emergency-communication systems and services.
–Michael Fowler
A few years ago, a harrowing situation unfolded when a witness reported a violent car accident on a busy highway. The caller dialed 911 on his cell phone, automatically activating the existing “Enhanced 9-1-1” (E9-1-1) system. The caller, unsure of where he was on the long highway, struggled to convey the accident’s precise location. The first responders were forced to physically locate the chaotic, tangled scene, delaying their arrival and their reaction to the emergency. The lack of accurate location data had hindered these first responders from reaching the scene promptly, exacerbating the risks and damage to the accident’s victims.
A few months later and several hundred miles away, a similar accident occurred. This time, however, the caller’s smartphone automatically connected to the new “Next Generation 9-1-1” (NG9-1-1) system, which transmitted not only the voice call but also precise GPS coordinates, real-time video, and additional contextual information to the emergency-services center. This richer data stream facilitated faster and more informed decision-making, enabling the first responders to navigate the complex highway system efficiently and providing critical details that significantly improved the time and efficiency of this emergency response.
The contrast between these two incidents illustrates the transformative impact of transitioning from Enhanced 9-1-1 to Next Generation 9-1-1. The enhanced capabilities of NG9-1-1, incorporating multimedia data and improved location accuracy, are proving instrumental in minimizing response time and optimizing emergency services’ effectiveness, ultimately making a substantial difference in potentially life-threatening situations.
The transition from traditional E9-1-1 to cutting-edge NG9-1-1 systems represents a significant leap forward in the communication capabilities and efficiency of emergency services. Understanding the distinctions between these two systems is crucial for appreciating the advancements that NG9-1-1 brings and why these differences are vital for modern emergency response.
E9-1-1: The Legacy Foundation of Emergency Communications
Enhanced 9-1-1 (E9-1-1) has long been the backbone of emergency communications, allowing people to seek help quickly during critical situations. It was built on legacy analog telephone technology and was designed purely to support voice communications over copper-based telephone networks.
The primary characteristic of E9-1-1 is its voice-centric nature. Typically, a distressed caller dialing 9-1-1 would speak with a dispatcher, who would gather essential information and coordinate an emergency-services response.
But E9-1-1 also integrated automatic location information. This feature allowed emergency responders to accurately pinpoint the caller’s location, a crucial factor in expediting response times. Whether the emergency occurred at home, at work, or on the road, the ability to locate a caller quickly and precisely often meant the difference between life and death. E9-1-1 has been instrumental in saving countless lives by coordinating the process of reporting emergencies and dispatching aid promptly.
However, the limitations of E9-1-1 gradually become apparent as technology advances and communication methods evolved beyond traditional voice calls. The need for a more versatile and comprehensive emergency-communication system led to the development of Next Generation 9-1-1 (NG9-1-1).
NG9-1-1: Embracing Multimedia and Data Integration
Next Generation 9-1-1 (NG9-1-1) represents a quantum leap in emergency communication, offering a broad array of capabilities far beyond its predecessor’s voice-centric model. NG9-1-1 is built on the current fiber-based Internet Protocol (IP) networks, which allows the caller’s location information to be conveyed within the Voice over IP (VoIP) call. The primary distinguishing feature of NG9-1-1 is its ability to handle—in addition to traditional voice calls—diverse types of data and multimedia, including text messages, images, videos, and other forms of digital information, all of which can be shared via the same connection with 9-1-1 telecommunicators and first responders.
The shift to an IP-based infrastructure is fundamental to NG9-1-1. This transition enables seamless integration of various communication methods, fostering a more dynamic and responsive emergency system. With the prevalence of smartphones and the increasing reliance on digital communication, NG9-1-1 is well-equipped to meet the evolving needs of the public.
In addition to supporting a broader range of communication methods, NG9-1-1 dramatically improves location accuracy. While E9-1-1 laid the groundwork for providing location information, NG9-1-1 offers much more precise and detailed location data, even within a large building—data particularly crucial in scenarios where callers may not be able to provide their location verbally, such as during medical emergencies or instances of criminal activity.
Why Do These Differences Matter?

The differences between E9-1-1 and NG9-1-1 are not merely technical nuances; they hold profound implications for emergency response and public safety.
- Versatility and Accessibility: NG9-1-1’s ability to handle various forms of communication ensures that individuals can seek help using methods that suit their situations. Text messages, images, and videos convey critical information that might be impossible to communicate when speaking is impossible or silence is imperative.
- Enhanced Response Times: NG9-1-1’s multimedia capabilities and improved location accuracy contribute significantly to faster and more effective emergency responses. Using NG-1-1, emergency services can receive real-time data, accurately assess situations, and dispatch appropriate resources with great precision, ultimately saving precious time in critical situations.
- Adaptability to Evolving Technologies: NG9-1-1’s IP-based infrastructure makes it flexible and adaptable to technological developments. The system will evolve alongside emerging technologies, providing a future-proof framework that will remain viable and effective for years to come.
- Improved Situational Awareness: NG-1-1’s integration of multimedia elements allows emergency responders to gain a more comprehensive understanding of the situation. Visual information from images or videos can provide critical context, aiding responders in making informed decisions and better preparing for the nature of the emergency.
- Indoor Location Services: NG9-1-1’s ability to provide detailed indoor location information is a game-changer, especially in large-building emergencies or situations when individuals cannot verbally communicate their whereabouts. This feature enhances the precision of emergency responses, particularly in densely populated areas with complex building structures, such as barracks on military installations.
The differences between E9-1-1 and NG9-1-1 underscore the dramatic evolution of emergency communication from a voice-centric model to a versatile, multimedia-enabled structure. These advances address the need to keep abreast of new technological developments, provide more responsive emergency services, and save lives in an increasingly interconnected and dynamic world. As NG9-1-1 continues to be adopted across more organizations, it’s paving the way for greatly improved emergency responses in all environments.
The Crucial Role of Redundant Connections

– Michael Fowler
Last month, more than 10 million Australians—nearly half the population—were left without mobile and internet service after a network failure at Optus, the country’s second-largest telecommunications provider. The outage caused transport delays, cut hospital phone lines, and shut down payment systems for almost 12 hours, effectively paralyzing thousands of businesses. Experts initially speculated that a cyber-attack had caused the blackout; ultimately, a network firmware patch was blamed for taking down the network. Optus had to physically dispatch technicians to remote parts of the country to reverse the patch installation.
The implications of this outage were profound for the day-to-day operations of companies solely reliant on Optus for telecommunications service, and it raises questions about the fragility of Australia’s core infrastructure. Productivity plummeted as employees lost the ability to share documents, communicate through email, and work together in real time.
In September, the global business community faced substantial disruption as Google Workspace—a comprehensive suite of productivity tools and collaborative services—experienced a widespread service failure. The outage lasted roughly 12 hours and was ultimately tracked to technical issues within Google’s infrastructure. During this period, users across the globe encountered difficulties accessing essential services such as Gmail, Google Drive, and Google Docs, hampering routine communication and collaboration efforts.
The loss of these services underscored the vulnerability of single-sourcing access to internet-based data, prompting organizations to reevaluate their dependency on single providers and consider diversifying their digital infrastructures to mitigate such risks.
The Risks of Single-Connection Dependency
Today’s interconnected businesses operate in a global marketplace where downtime can translate into lost revenue, damage to reputation, and disrupted operations. Depending on a single ISP for internet access creates a single point of failure, leaving the business vulnerable to network outages, hardware failures, and cyberattacks.
There are almost as many causes for service disruption as elements in the telecom stream, from coding errors to vulcanism on the sea floor. Here are a few of the more dramatic recent disruptions to internet-based data and services:
Comcast Outage
In 2017, Comcast, one of the largest ISPs in the United States, experienced a widespread outage of its internet service, Xfinity, that affected businesses and residential users nationwide. The blackout—caused by a minor configuration error—left users without internet access for several hours. Companies relying solely on Comcast Xfinity for their connectivity faced wide-ranging disruptions in their day-to-day online operations, highlighting the vulnerabilities of a single-connection arrangement.
Level 3 Communications Outage
Level 3 Communications, a major global telecommunications company, suffered a significant outage in 2016 when one of its technicians left a field blank on an electronic form. The resulting shutdown led to widespread disruptions of popular websites and online platforms. The outage also affected approximately 29.4 million VoIP users and about 2.3 million wireless users; the total tally of calls that failed to go through exceeded 111 million, according to a later investigation by the FCC. The nationwide outage lasted nearly an hour and a half, during which businesses relying on Level 3 faced significant potential service disruptions and financial losses.
Dyn DNS Cyberattack
On October 21, 2016, three consecutive, massive distributed denial-of-service (DDoS) attacks targeted Dyn, a company that controls much of the internet’s domain name system (DNS) infrastructure. The attacks, executed using botnets, brought down much of America’s internet, affecting popular sites and services such as Twitter, Reddit, Amazon, and Netflix. Businesses relying on Dyn for DNS services found their online presence crippled during the attack. This incident highlighted the vulnerability of depending on a single DNS provider for internet connectivity.
Mitigating the Risks: The Role of Redundancy
So, how do businesses keep their operations running smoothly in the face of unexpected events? The answer lies in redundancy. A redundant internet connection serves as a backup in case of primary connection failure. Businesses can achieve redundant internet connectivity through various methods, including having multiple internet service providers (ISPs) and using a cellular connection as backup. Redundancy helps mitigate the risks associated with single points of failure and enhances business continuity. Among the advantages of redundant internet access are:
High Availability:
Redundant connections provide high availability by ensuring that a secondary link can seamlessly take over during an outage of the primary ISP. Redundancy minimizes downtime and allows business operations to continue uninterrupted.
Load Balancing:
Redundant connections allow load balancing and distribute network traffic across multiple connections. Load balancing enhances performance and prevents congestion, reducing the likelihood of slowdowns or service interruptions.
Diverse Pathways:
Utilizing multiple ISPs or diverse network paths offers protection against localized outages or infrastructure failures. If a specific geographic area or network segment experiences issues, redundant connections can provide alternative routes to maintain connectivity.
Resilience Against Cyberattacks:
Redundant connections can offer protection against cyberattacks by isolating and mitigating the impact of an attack on one connection. In the event of a DDoS attack targeting one ISP, the redundant connection can help absorb the malicious traffic and keep essential services running.
The importance of having redundant internet access connections cannot be overstated in today’s digitally driven business landscape. The risks of relying on a single ISP are evident from real-world examples of outages and cyberattacks. Redundancy provides high availability and resilience against failures and safeguards businesses against the potentially devastating consequences of downtime. As the digital landscape evolves, these measures will become increasingly essential for businesses to thrive in an interconnected and dynamic environment.
SD-WAN is Simplifying Network Management and Saving Companies a Fortune
Walmart, Inc., is the world’s largest company and the world’s largest private employer. With eleven thousand stores worldwide, its networking requirements are among the most challenging you can find in the private sector. A few years ago, the retail giant was seeking a better point-of-sale (POS) experience and an improvement in its on-the-shelf inventory—two sure ways to enhance customer satisfaction.
Recognizing that it needed to allocate its network traffic more efficiently, Walmart transitioned to a software-defined wide area network (SD-WAN), which assigned special priority to processes directly affecting the customer experience—things like POS and inventory-management systems—while shunting less time-critical data through slower, less expensive connections.
The new SD-WAN system also allowed Walmart to monitor and manage its network in real time from a centralized location, reducing the need for on-site administrative and technical support. By decreasing its reliance on expensive legacy systems and a nationwide army of administrative IT personnel, this consolidation of network-management functions has boosted the productivity of Walmart’s technology infrastructure and substantially reduced its operating expenses.
What is SD-WAN?
The explosive growth in digital connectivity is driving many businesses to look for faster, more dependable, more cost-effective solutions to their networking requirements. Traditionally, wide area networks (WANs) were assembled around expensive and inflexible hardware; managing them required a significant amount of time-consuming manual configuration and monitoring by human administrators.

SD-WAN represents a revolutionary paradigm in network management. This rapidly expanding model simplifies the oversight and operation of wide area networks (WANs) by introducing a software-driven, abstracted framework for network hardware and control functions. This transformation yields numerous advantages, including enhanced performance, streamlined network administration, and substantial cost savings.
In essence, SD-WAN decouples the physical infrastructure of a network from its administrative and control components. This abstracted, software-based model for managing and overseeing a network provides businesses with the potential for greater adaptability and scalability, all while reducing operational expenses.
SD-WAN relies on a few central features and capabilities to deliver intelligent network routing, traffic optimization, and cybersecurity services.
The Features and Benefits of SD-WAN
- Centralized Control: SD-WAN allows organizations to centralize network management and control. A single administrator can oversee and manage the entire network comprehensively through a unified dashboard. This simplifies monitoring, configuration, and organization while facilitating the implementation of policies and network changes. For example, centralized control allows administrators to set rules prioritizing specific traffic types—such as VoIP or video conferencing—over less critical data. And centralized control has been shown to reduce troubleshooting response time by up to 70%.
- Overlay Network: SD-WAN creates a logical overlay network on top of the existing physical network infrastructure. The overlay network can be encrypted and is independent of the underlying physical network, simplifying management and optimization. New virtual topologies can be established without modifying the WAN hardware.
- Dynamic Path Selection: SD-WAN continuously evaluates available private and public network paths and selects the most appropriate route for network traffic by assessing available bandwidth, current latency, and network traffic to ensure that critical applications receive the resources necessary for peak performance.
By optimizing traffic paths and reducing reliance on expensive Multiprotocol Label Switching (MPLS) connections, this process can reduce network costs by up to 90% when compared to traditional WAN solutions.
- Application-Aware Routing: SD-WAN also recognizes and prioritizes traffic based on application category, enabling businesses to allocate resources to mission-critical applications over less critical traffic (e.g., email or web browsing).
- Security Integration: Some earlier versions of SD-WAN did not place any great emphasis on security, but competition and demand have driven SD-WAN providers to offer increasingly comprehensive cybersecurity measures with their solutions. These include Next Generation Firewall (NGFW) systems, Security Gateway Appliances, and Cloud Network Security as a Service. These security measures are crucial for protecting sensitive information and preventing cyberattacks.
- Cloud Integration: Many SD-WAN systems are cloud-ready by default, allowing businesses to connect to cloud-based services and data centers with virtually no effort.
- Network Flexibility: SD-WAN is an inherently flexible and centrally controlled technology, so making rapid changes and additions to the network is a simple matter.
According to IDC, 65% of businesses adopting SD-WAN are doing so to enhance network flexibility and agility. SD-WAN eliminates reliance on a single service provider or network architecture, allowing companies to “mix and match” network links—including broadband, 4G/5G, and MPLS—to create flexible, resilient, and cost-effective WAN infrastructures.
Adding new branches or locations is a straightforward process, and the overlay network can accommodate network growth without extensive configuration changes. This scalability is particularly beneficial for businesses planning to expand or those with fluctuating network demands.
- Robust Business Continuity: SD-WAN’s ability to dynamically reroute traffic in case of network failure or congestion enhances business continuity. This resilience is invaluable for ensuring that critical operations continue uninterrupted.
Delta Airlines
Like Walmart, Delta Airlines adopted an SD-WAN architecture to streamline operations and cut costs. Major carriers like Delta require tremendously robust network infrastructures to handle a mass of complex processes, including passenger check-in, baggage handling, and—most critically—flight tracking. Delta incorporated SD-WAN to optimize its network traffic by allocating greater bandwidth to mission-critical applications and routing less time-sensitive information through more cost-effective connections like broadband and LTE. The move to SD-WAN improved the performance of Delta’s network processes and significantly reduced operational costs by lowering Delta’s reliance on its expensive Multiprotocol Label Switching (MPLS) connections.
Walmart’s and Delta’s adoption of SD-WAN showcase the transformative power of this technology in large, indispensable industries, enhancing both consumer experience and operational efficiency while resulting in substantial cost savings.
So, SD-WAN technology is emerging as a game-changer for enterprises of any size seeking to improve network performance, reduce costs, and simplify network management. It provides the agility and efficiency to thrive in today’s competitive landscape by centralizing control, optimizing traffic, and integrating network cybersecurity measures.
The message is becoming clear: If you want to stay ahead of the curve and maintain your competitive edge in the digital era, embracing SD-WAN is rapidly becoming a strategic imperative.

VoIP offers the healthcare industry multiple communication options, greater information security, and enhanced care delivery for patients all while keeping your information secure and within HIPAA compliance.
-Michael Fowler
Effective communication is vital in the healthcare industry, and staying up-to-date with the latest technology is crucial. That’s why healthcare institutions are turning to the latest Voice over Internet Protocol (VoIP) systems—such as 3CX, Avaya IP Office, and Mitel MiCloud Connect—for innovative new ways of operating and delivering healthcare services.
A Versatile Communications Platform
Modern VoIP systems are Unified Communications (UC) platforms, meaning they combine organizational communication channels. They bring voice calls, video conferencing, instant messaging, and more under one user-friendly roof. Their adaptability makes them a standout choice for healthcare organizations of all sizes. Voice over Internet Protocol systems provide:
- High-Quality Internet-Based Voice Calls: Because VoIP technology delivers high-quality voice communication over the internet, doctors, nurses, and support staff can make clear calls regardless of location.
- Video Conferencing: With the surge in telemedicine and remote consultations, video-conferencing capabilities allow healthcare providers to conduct virtual meetings, share medical records, and perform remote diagnostics, boosting efficiency and improving patient access to care.
- Instant Messaging: Secure instant messaging provides rapid information exchange among healthcare professionals. It’s perfect for discussing patient cases, sharing updates, and addressing urgent matters in real time.
- Seamless Integration with Electronic Health Records (EHR): EHRs are the lifeblood of modern healthcare, housing vital patient data, treatment histories, and diagnostic records. 3CX’s integration with Electronic Health Records (EHR) systems is a particular advantage, allowing, healthcare providers access to patient data instantly during consultations, reducing errors and ensuring comprehensive patient care.
The Benefits of VoIP for Healthcare Organizations

Improved Patient Care and Safety
In healthcare settings, effective communication is a necessity for ensuring the highest level of patient care and safety. VoIP solutions empower healthcare professionals to collaborate in real time, share vital patient information securely, and make informed decisions swiftly. Doctors and specialists can conduct video consultations for fast remote assessments and diagnoses. Nurses and pharmacists can easily confer about medication orders, dosages, and patient allergies, reducing the risk of medication errors.
Enhanced Staff Collaboration
Teamwork is absolutely central to the field of healthcare. High-end VoIP fosters collaboration among healthcare professionals by providing them the tools to work together seamlessly. Departments within a healthcare institution can communicate effortlessly, ensuring everyone is on the same page regarding patient care plans and progress.
Training and Continuing Education
Solutions like 3CX VoIP facilitate virtual training sessions and conferences, allowing healthcare professionals to stay updated on the latest medical advancements and best practices.
Cost Savings
With healthcare expenses continually rising, cost-effective solutions can be worth their weight in gold. VoIP systems offer many opportunities ways for healthcare institutions to save money, including:
- Reduced Infrastructure Costs: VoIP systems are software-based and can run on existing hardware, eliminating costly investments in specialized communication equipment.
- Lower Telecommunication Costs: VoIP technology slashes long-distance call charges, a boon for institutions that must communicate with patients and colleagues across vast geographic areas.
- Streamlined Administration: The technology’s centralized management interface simplifies administrative tasks, reducing the need for a vast IT staff and its associated expenses.
Security and HIPAA Compliance
Adherence to the laws and regulations mandating patient-data security is non-negotiable. Features such as secure messaging and encryption ensure that healthcare institutions maintain compliance with the Health Insurance Portability and Accountability Act (HIPAA). All data transmitted over VoIP is encrypted, safeguarding patient information from unauthorized access or breaches.
Ease of Transition
Training healthcare staff on a comprehensive new technology system can seem a daunting and somewhat unpleasant task. Surprisingly, however, healthcare organization have found the introduction of VoIP-based systems into their environments to be surprisingly seamless.
VoIP platforms offer user-friendly interfaces, making them easy for staff to navigate and use. Additionally, VoIP providers offer comprehensive training and support, ensuring that the healthcare staff is confident and skilled in using the new platforms. This ease of adoption has helped address many potential concerns about making for a smooth transition for healthcare institutions.
Rapidly Growing Adoption

Many prominent healthcare organizations have already implemented VoIP systems and are experiencing their benefits. St. Mary’s Hospital, in the heart of New York City, is a prime example of a healthcare institution that seamlessly integrated 3CX VoIP into its operations, reaping significant benefits. The hospital’s success with VoIP demonstrates how these systems can be a game-changer in a bustling urban healthcare environment. Mercy Health System, a large, multi-hospital network based in Pennsylvania, has harnessed the power of 3CX VoIP to optimize patient care and staff collaboration across its sprawling healthcare network. The adaptability and scalability of VoIP systems make them effective even for larger healthcare organizations.
In short, VoIP technology is already transforming the healthcare industry by revolutionizing the way institutions operate and provide their services.
Healthcare professionals find these systems highly valuable because of their exceptional range of different communication channels, effortless integration with EHR systems, and wide range of other benefits.
Healthcare institutions find VoIP technology attractive because it allows them to:
- Boost patient care and safety;
- Foster staff collaboration;
- Save costs; and
- Stay compliant with healthcare regulations.
As the healthcare environment continues to evolve, VoIP technology can serve as a powerful element in the delivery of efficient, cost-effective, highest-quality patient care.
The Crucial Role of Tackling Insider Threats to Your Cybersecurity

-Michael Fowler
In today’s interconnected digital reality, the battle to secure sensitive data and maintain the integrity of computer systems has never been more critical. But while the security spotlight often shines outward toward external hackers and malicious software, there’s another, much closer peril deserving your keen attention: Insider Threats.
Case Study
In 2018, a disgruntled Tesla employee used false usernames to change a vital element of the company’s manufacturing operating code. He also exported gigabytes of sensitive data, including trade secrets, to unknown third parties.
His motive for the attack? Revenge. He had expected a promotion, did not receive it, and decided to use his insider privileges to damage and sabotage the company.
Following the sabotage and data leak, Tesla’s share prices fell by five percent, and a production ramp-up was significantly delayed. (Source: RiskOptics)
The Nature of Insider Threats
An insider threat is usually a trusted individual or privileged user—an employee, vendor, contractor, associate, or business partner—authorized admission into an organization’s IT assets and information. Because of their access and familiarity with an organization’s systems, these users have the potential to exploit vulnerabilities, compromise cybersecurity, and cause significant damage with relative ease.
Insider threats come in various forms, each possessing its own potential to rupture an organization’s information security fabric. They can arise from employees who are dissatisfied and intentionally acting out, as well as from uninformed individuals who are unintentionally careless.
In terms of maintaining a robust cybersecurity posture, the importance of identifying these insider threats and thwarting the damage they can cause cannot be overstated.
The following are the three most common categories of insider threat:
- Malicious Insiders: These are individuals who misuse their internal privileges with malicious intent. Their motives can range from personal gain to revenge, and their actions can result in severe consequences, such as the data breaches and system sabotage that Tesla suffered.
- Negligent Insiders: These insiders may not harbor any ill intentions, but their actions can compromise cybersecurity nevertheless. From falling prey to phishing attacks to unwittingly sharing sensitive information, their slip-ups can pave the way for unauthorized access to sensitive information.
- Compromised Insiders: In these cases, external actors manipulate an insider’s credentials to gain unauthorized entry into the organization’s IT infrastructure. This possibility underscores the importance of monitoring employee behavior and scrutinizing unusual network activities that might indicate a compromised insider.
The Power of Early Identification
The first line of defense in thwarting insider threats is identifying them as early as possible. Detecting insider threats involves closely observing employee behavior, tracking network activity, and recognizing patterns that could indicate an impending breach. Early identification is crucial for several reasons:
- Swift Intervention: By spotting suspicious activity promptly, organizations can intervene and mitigate potential threats before they escalate into full-blown crises. Detecting anomalies in data access, unusual log-in patterns, or uncommon data transfers can help flag potential insider threats.
- Tailored Risk Management: Identifying insider threats early on enables organizations to assess the severity of the situation and allocate resources accordingly. The organization can then take targeted, appropriate security measures as appropriate.
- Escalation Prevention at an Early Stage: Organizations can often eliminate the motivations for malicious actions by addressing the root causes of insider threats. Tackling employee dissatisfaction, enhancing training, and shoring up system vulnerabilities can significantly lower the potential for hostile activity.

Strategies for Preventing Insider Threats
Effective prevention of insider threats requires a multifaceted approach combining technological solutions, well-established policies, and a pervasive culture of security awareness. Here are some preventive methods to consider:
1. Controlled Access and Privilege Management: Limiting access to sensitive data based on an individual’s roles and responsibilities helps minimize the risk of data misuse. Rigorous access controls and regular privilege reviews ensure that employees only have access to the information relevant to their tasks.
2. Security Training and Vigilance: Educating employees about cybersecurity and the perils of insider threats is essential. Regular training sessions enable employees to identify phishing attempts, comprehend secure password practices, and promptly report any suspicious activities.
3. Surveillance and Analytics: Utilize advanced monitoring tools that analyze both employee actions and network activities to reveal anomalies. These tools can generate alerts for potential insider threats and provide valuable insights leading to further investigation.
4. Incident Response Planning: A well-defined incident response plan streamlines the process of addressing suspected insider threats. The plan should delineate protocols for investigating incidents, managing risks, and transparently communicating with stakeholders.
5. Encouraging Open Reporting:
Cultivating an environment where employees feel comfortable reporting unusual activity without fear of reprisal can go a long way. Establish anonymous reporting channels, which encourage open dialogue and timely threat reporting.
6. Continuous Evaluation:
Regularly assessing and refining your organization’s security policies and procedures allows you to adapt to the evolving threat environment. Security audits and risk assessments will help identify potential vulnerabilities and areas needing improvement.
7. Fostering a Culture of Cybersecurity
An impregnable defense against insider threats hinges on fostering a culture steeped in security consciousness across the organization. Elements of an organizational culture of cybersecurity consciousness might include:
Effective prevention of insider threats requires a multifaceted approach combining technological solutions, well-established policies, and a pervasive culture of security awareness. Here are some preventive methods to consider:
1. Controlled Access and Privilege Management: Limiting access to sensitive data based on an individual’s roles and responsibilities helps minimize the risk of data misuse. Rigorous access controls and regular privilege reviews ensure that employees only have access to the information relevant to their tasks.
2. Security Training and Vigilance: Educating employees about cybersecurity and the perils of insider threats is essential. Regular training sessions enable employees to identify phishing attempts, comprehend secure password practices, and promptly report any suspicious activities.
3. Surveillance and Analytics: Utilize advanced monitoring tools that analyze both employee actions and network activities to reveal anomalies. These tools can generate alerts for potential insider threats and provide valuable insights leading to further investigation.
4. Incident Response Planning: A well-defined incident response plan streamlines the process of addressing suspected insider threats. The plan should delineate protocols for investigating incidents, managing risks, and transparently communicating with stakeholders.
5. Encouraging Open Reporting:
Cultivating an environment where employees feel comfortable reporting unusual activity without fear of reprisal can go a long way. Establish anonymous reporting channels, which encourage open dialogue and timely threat reporting.
6. Continuous Evaluation:
Regularly assessing and refining your organization’s security policies and procedures allows you to adapt to the evolving threat environment. Security audits and risk assessments will help identify potential vulnerabilities and areas needing improvement.
7. Fostering a Culture of Cybersecurity
An impregnable defense against insider threats hinges on fostering a culture steeped in security consciousness across the organization. Elements of an organizational culture of cybersecurity consciousness might include:
- Leading by Example;
- Consistent Communication;
- Incentives for Vigilance;
- Cross-Functional Collaboration; and
- Lifelong Learning.
In the cybersecurity arena, insider threats present a formidable challenge. But through a blend of proactive identification, robust prevention strategies, and a steadfast culture of security awareness, organizations can fortify their cybersecurity defenses against both internal and external adversaries. The mission to safeguard our digital domain begins within our own walls.
In the cybersecurity arena, insider threats present a formidable challenge. But through a blend of proactive identification, robust prevention strategies, and a steadfast culture of security awareness, organizations can fortify their cybersecurity defenses against both internal and external adversaries. The mission to safeguard our digital domain begins within our own walls.

